Empower
teams with AI
Achieve your online education goals with Automation Academy.


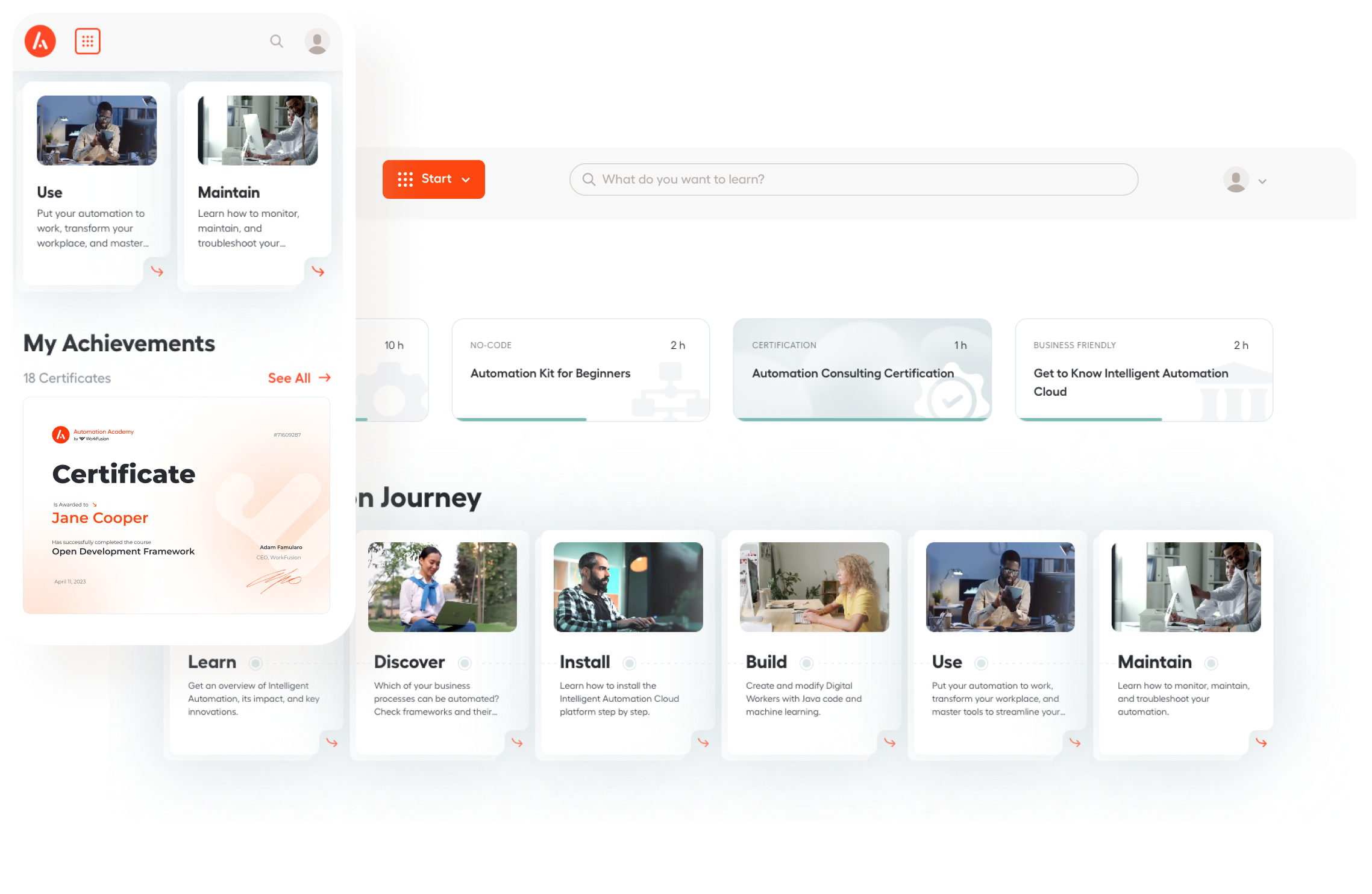
All-in-one platform
Learn, practice, and test your new automation skills.

- Courses tailored to each role
- Hands-on training with our automation platform
- Step-by-step video tutorials
- Shareable digital certificates
- Assignments that replicate typical automation scenarios
- 24/7 support
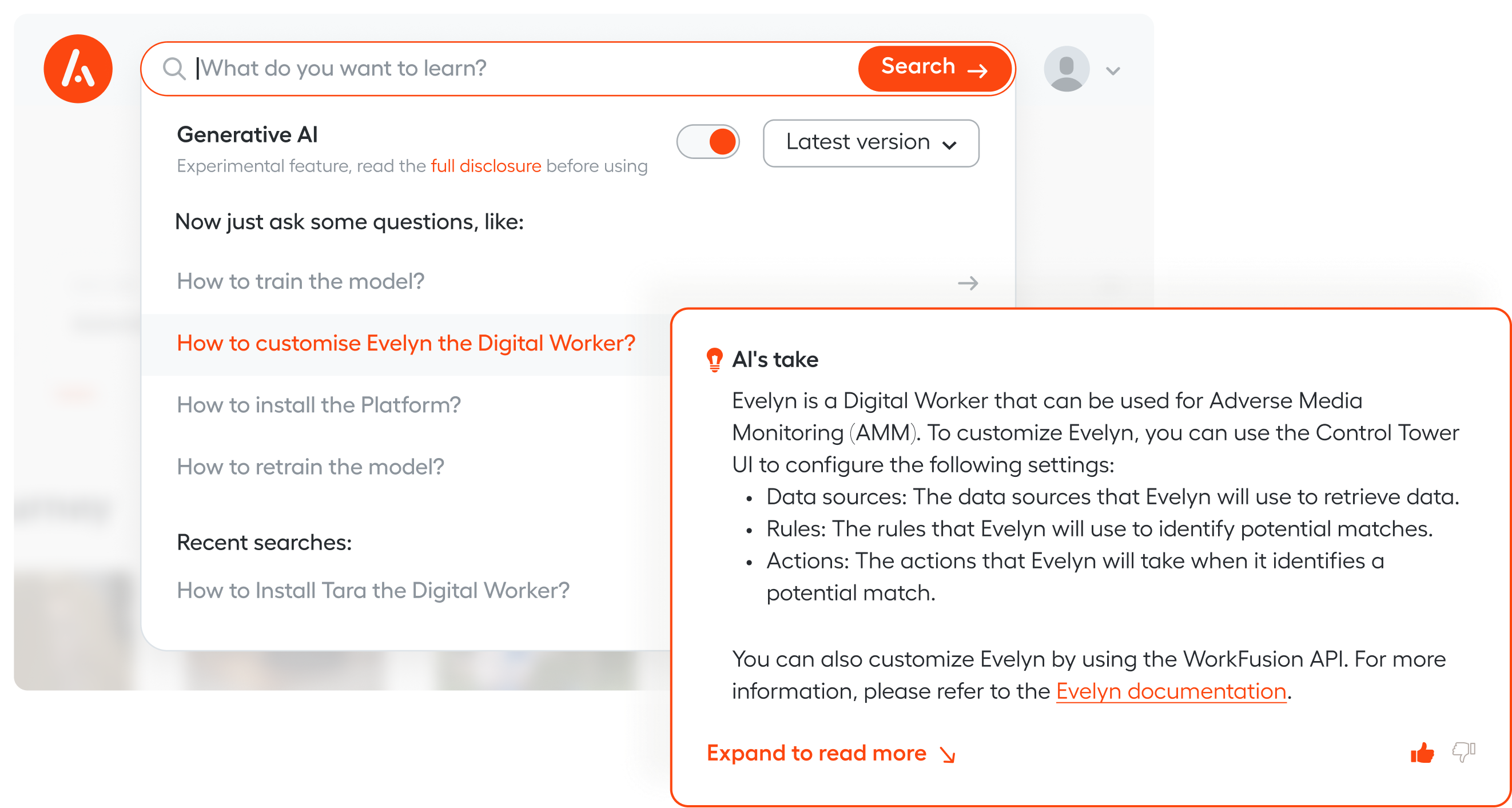
Ask questions —
get answers
Introducing a new generation of search powered by generative AI. Let it immerse you in the Intelligent Automation world and boost the adoption of AI-infused Digital Workers.
Introducing a new generation of search powered by generative AI.

Let it immerse you in the Intelligent Automation world and boost the adoption of AI-infused Digital Workers.
Upskill the entire team
Whether you’re a business user or developer, gain advanced automation skills.
Developers
Role-based training for all members of an automation team — from RPA Developers to Machine Learning Engineers and Data Analysts.
Operations
Automation training for operations specialists on how to identify strong automation use cases and turn business requirements into automated workflows.
Analysts
On-demand courses discuss automation approaches, best practices, and business benefits. Designed for forward-thinking leaders in banking, insurance and other industries.
IT
Designed for Platform Management and Support teams to learn how to set up, configure, monitor, manage and troubleshoot the platform.

for Programs

for Roles

for Courses
Welcome to class: In-person automation training
Customized and advanced automation training to level up your Center of Excellence.
Get started with out-of-the-box Digital Workers
After selecting Digital Worker(s) to join your team, learn how to work with your new colleague(s) and master platform capabilities.
Learn moreBuild your automation Center of Excellence
Build delivery, platform, and consulting teams that form your Automation CoE, which creates, modifies, and maintains Digital Workers.
Learn moreYour partner in digital transformation
Enterprise customers train with us and achieve automation success.
1,200+
hours of curriculum
50+
courses
We are already using robots in the insurance business. Thanks to the combination of Robotic Process Automation (RPA) and Artificial Intelligence, we are now able to intelligently automate the entire process end-to-end.
HDI Versicherung
50,000+
trainees
80%
trainees graduated